This information supplies a complete evaluation of web site whitelisting. We’ll discover what it’s, why it’s recommended, and supply detailed, step by step directions for enforcing it throughout more than a few platforms and units. Whether or not you’re a guardian taking a look to give protection to your kids, a enterprise proprietor securing your community, or simply anyone who desires extra regulate over your virtual existence, this text gives you the data you want.
Key Takeaways
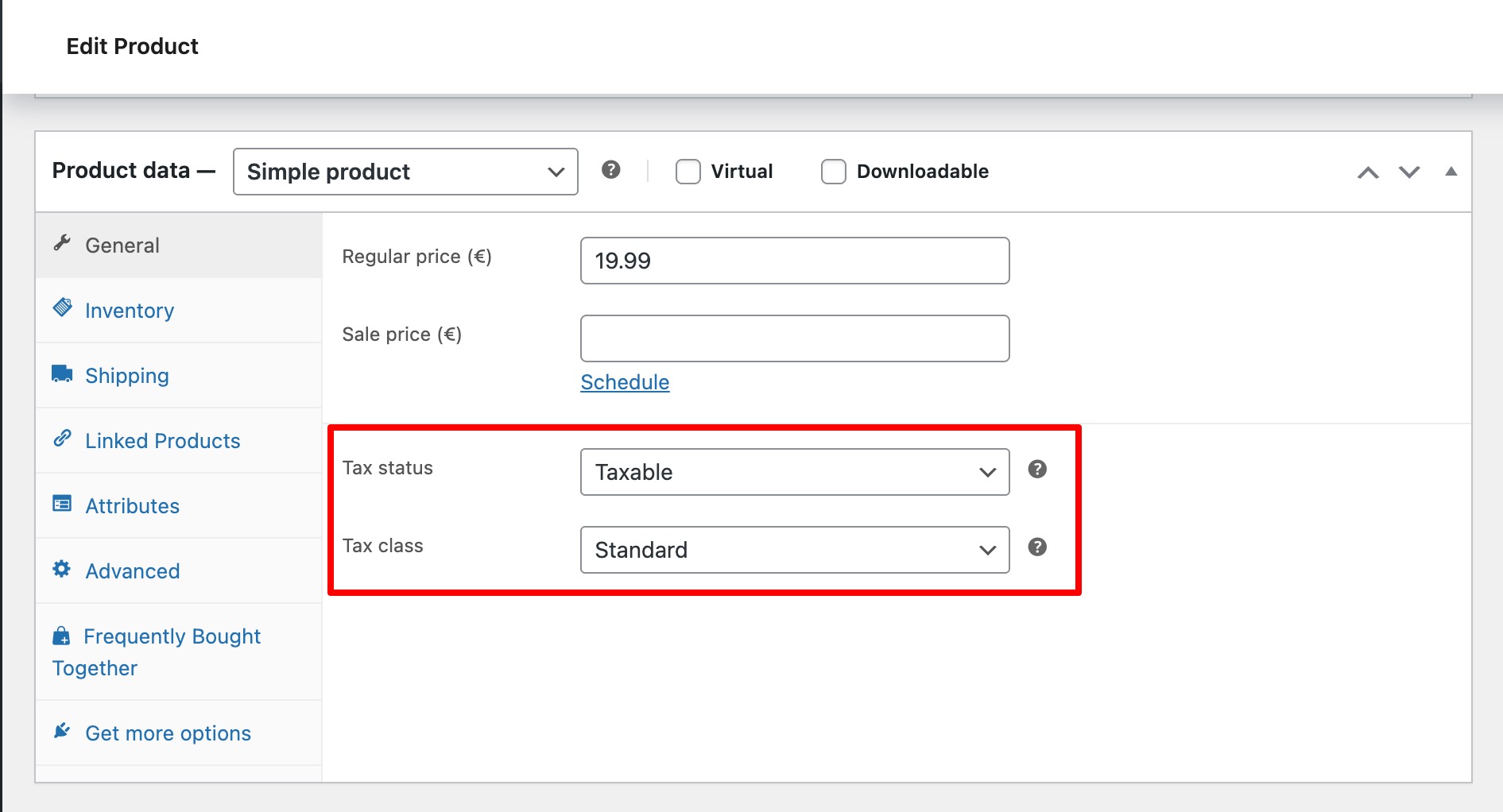
- What’s Whitelisting? Whitelisting is a safety technique that grants get right of entry to solely to pre-approved web sites, IP addresses, or packages, blocking off all others by way of default. This “default deny” method is extra restrictive and protected than blacklisting, which solely blocks recognized threats.
- Why Whitelist? The principle advantages come with enhanced safety in opposition to malware and phishing, stepped forward productiveness by way of restricting distractions, content material regulate for kids, and making sure community compliance in a enterprise surroundings.
- How Does it Paintings? Whitelisting will also be carried out at more than a few ranges, together with on particular person browsers, working methods, routers, and thru devoted safety device. Every way provides other ranges of regulate and complexity.
- Step-by-Step Guides: This text supplies detailed directions for putting in place whitelists on common platforms like Google Chrome, Firefox, Home windows, macOS, Android, iOS, and on community routers.
- Opting for the Proper Means: The most efficient whitelisting technique is dependent upon your particular wishes. For private use, browser or OS-level controls would possibly suffice. For households or companies, router-level or devoted device answers be offering extra complete coverage.
Figuring out Web site Whitelisting
Ahead of we dive into the “how,” let’s identify a cast figuring out of the “what” and “why.” Whitelisting is a elementary idea in cybersecurity, however its utility can range considerably relying at the context.
What Is a Whitelist?
At its core, a whitelist is an unique listing of accepted entities. Within the context of web sites, it’s a curated listing of URLs {that a} person or components is permitted to get right of entry to. Any web site no longer in this listing is robotically blocked.
Bring to mind it like a visitor listing for an unique occasion. In case your identify is at the listing, the bouncer means that you can in. If it’s no longer, you’re denied access, without reference to who you’re. A blacklist, alternatively, is sort of a listing of troublemakers who’re particularly banned from the occasion. Everybody else is permitted in, which is a miles much less protected method as a result of you’ll’t perhaps know each and every doable troublemaker upfront.
This “default deny” posture is the important thing differentiator and the supply of whitelisting’s power. It assumes all unknown web sites are doable threats till they’re explicitly verified and added to the accepted listing.
Whitelisting vs. Blacklisting: A Story of Two Safety Fashions
To completely admire whitelisting, it’s useful to check it at once with its extra commonplace counterpart, blacklisting.
| Characteristic | Whitelisting (Default Deny) | Blacklisting (Default Permit) |
| Means | Simplest permits get right of entry to to pre-approved web sites. | Blocks get right of entry to solely to recognized malicious or unwanted web sites. |
| Safety Degree | Prime. Proactively blocks new and unknown threats (zero-day assaults). | Average. Reactive. It can not give protection to in opposition to threats that haven’t been recognized and added to the listing but. |
| Upkeep | Extra in depth in advance. Calls for construction and keeping up a listing of all vital web sites. | Much less in depth first of all. Lists are regularly pre-populated by way of safety distributors, however require consistent updating as new threats emerge. |
| Person Revel in | May also be restrictive. Customers could also be blocked from authentic new websites till they’re reviewed and added. | Extra versatile. Customers can get right of entry to lots of the web with out restriction, which additionally will increase possibility. |
| Best possible Use Case | Managed environments: kids’s units, company networks with particular activity purposes, kiosk computer systems. | Basic-purpose surfing the place flexibility is prioritized over most safety. |
As cybersecurity knowledgeable Itamar Haim notes, “Blacklisting is like seeking to patch each and every hollow in a sinking send, whilst whitelisting is like crusing in a submarine. The previous is a continuing, reactive battle in opposition to an never-ending sea of threats. The latter supplies a essentially protected surroundings from the outset.”
The Advantages of Whitelisting a Web site
Imposing a whitelist provides a number of tough benefits that transcend simply blocking off malicious websites.
- Unequalled Safety: That is probably the most vital get advantages. Whitelisting supplies powerful coverage in opposition to quite a lot of cyber threats, together with:
- Malware and Ransomware: Customers can not unintentionally navigate to web sites web hosting malicious device.
- Phishing Scams: Phishing websites, designed to thieve credentials, are blocked by way of default until they by some means get accepted.
- 0-Day Exploits: Those are assaults that exploit up to now unknown vulnerabilities. Since blacklists don’t find out about them, they may be able to’t block them. A whitelist blocks them inherently since the malicious web site isn’t at the accepted listing.
- Enhanced Productiveness: In a enterprise or tutorial surroundings, the web could be a main supply of distraction. Social media, information websites, and leisure platforms can eat hours of productive time. Whitelisting permits employers and educators to limit get right of entry to to just the ones web sites very important for paintings or find out about, making a targeted virtual surroundings.
- Content material Regulate and Kid Protection: For fogeys, whitelisting is top-of-the-line approach to create a protected on-line “walled lawn” for kids. You’ll be able to curate a listing of age-appropriate tutorial websites, video games, and video platforms, making sure your youngsters aren’t uncovered to irrelevant or destructive content material.
- Community and Bandwidth Control: In a company surroundings, non-work-related streaming and downloads can eat vital community bandwidth, slowing down important enterprise packages. Whitelisting guarantees that bandwidth is reserved for authentic enterprise functions.
- Compliance and Coverage Enforcement: Many industries have strict regulatory necessities relating to knowledge safety and web utilization. Whitelisting is helping organizations put in force those insurance policies and display compliance by way of keeping up tight regulate over community get right of entry to.
Tips on how to Whitelist a Web site: Step-by-Step Directions
Now that we’ve lined the basics, let’s get into the sensible utility. We’ll stroll thru methods to arrange whitelists the use of other equipment and on other platforms, from internet browsers to all your community.
Means 1: Whitelisting in Internet Browsers
Most present internet browsers have integrated options or extensions that can be utilized to create a web site whitelist. This system is very best for controlling get right of entry to on a unmarried pc.
Google Chrome
Google Chrome doesn’t have a easy, integrated “whitelist-only” mode for normal surfing, however you’ll reach it the use of a mix of extensions and settings, in particular for controlled or supervised accounts.
The use of an Extension (e.g., BlockSite):
- Set up the Extension: Cross to the Chrome Internet Retailer and seek for “BlockSite” or a an identical site-blocking extension. Click on “Upload to Chrome.”
- Open Extension Choices: As soon as put in, click on the puzzle piece icon within the top-right of Chrome, in finding BlockSite, and click on the 3 dots, then “Choices.”
- Allow Whitelist Mode: Within the BlockSite dashboard, search for a “Whitelist” mode or a surroundings that claims “Block all websites apart from those I upload.” That is regularly a top rate function.
- Upload Your Authorized Websites: Input the URLs of the internet sites you need to permit (e.g., wikipedia.org, google.com) into the whitelist.
- Set a Password (Really useful): To forestall customers from merely disabling the extension or converting the settings, give protection to the choices with a password.
Video Information: Managing Chrome Extensions https://www.youtube.com/watch?v=sK7KajMZcmA
Mozilla Firefox
Very similar to Chrome, Firefox is determined by add-ons for complicated web site filtering and whitelisting.
- In finding an Upload-on: Cross to the Firefox Browser ADD-ONS retailer and seek for a content material blocker like “Block Web page” (a unique model than Chrome’s) or “LeechBlock NG.”
- Set up the Upload-on: Click on “Upload to Firefox” to put in your preferred extension.
- Configure the Whitelist:
- Open the add-on’s choices web page by way of right-clicking its icon within the toolbar.
- Search for a surroundings to create a “block set.” You’ll be able to configure this set to dam all web sites by way of the use of a wildcard personality (*).
- Then, in finding the “Whitelist” or “Exceptions” tab and input the internet sites you need to permit.
- You’ll be able to set particular instances for those regulations to be lively, which is excellent for productiveness.
- Give protection to the Settings: Get right of entry to to the add-on’s configuration can normally be password-protected to stop tampering.
Means 2: Whitelisting on Working Programs
Working system-level controls supply a extra powerful resolution than browser extensions as a result of they practice to all browsers and packages at the tool.
Home windows (The use of Circle of relatives Protection)
Microsoft Circle of relatives Protection is a formidable software for fogeys that incorporates powerful content material filtering and whitelisting features.
- Set Up a Circle of relatives Team:
- Cross to account.microsoft.com/circle of relatives.
- Check in along with your Microsoft account and create a circle of relatives staff.
- Invite your members of the family (or create a kid account). They are going to want their very own Microsoft accounts.
- Configure Content material Filters for a Kid Account:
- As soon as the kid account is ready up and added for your circle of relatives staff, in finding their identify within the Circle of relatives Protection dashboard and click on on “Content material filters.”
- Cross to the “Internet and seek” tab.
- Allow the “Filter out irrelevant web sites and searches” toggle.
- Crucially, permit the choice “Simplest let them talk over with those web sites.” This turns on whitelist mode.
- Construct Your Whitelist:
- Within the “Allowed websites” field, input the URLs of the internet sites you need to allow.
- Any try to talk over with a web site no longer in this listing will likely be blocked, and the person will find a way to request permission. You’re going to obtain a notification to approve or deny the request.
macOS (The use of Display screen Time)
Apple’s Display screen Time function, to be had on macOS, iOS, and iPadOS, supplies very good equipment for content material restriction and whitelisting.
- Open Gadget Settings: Click on the Apple icon within the top-left nook and pass to “Gadget Settings.”
- Navigate to Display screen Time: Make a selection “Display screen Time” from the sidebar. When you’re surroundings this up for a kid, be sure you’ve configured Circle of relatives Sharing and decided on the kid’s account.
- Cross to Content material & Privateness: Click on on “Content material & Privateness.”
- Prohibit Grownup Web pages: Below “Internet Content material,” make a choice the “Prohibit Grownup Web pages” possibility. This allows a fundamental filter out, however we wish to pass additional.
- Create the Whitelist:
- Click on the “Customise…” button.
- Below the “Allowed” segment, click on the + icon so as to add the particular URLs of web sites you need to permit.
- To create a real whitelist, you’ll upload a dummy access to the “Limited” listing. Extra successfully, for kids’s units, you’ll make a choice the “Allowed Web pages Simplest” possibility, which gives a pre-made listing of child-friendly websites that you’ll then customise.
Video Educational: The use of macOS Display screen Time https://www.youtube.com/watch?v=gvuy5vSKJMg
Means 3: Whitelisting on Cell Units
Cell units are regularly the main approach folks, particularly kids, get right of entry to the web. Right here’s methods to lock them down.
Android (The use of Google Circle of relatives Hyperlink)
Google Circle of relatives Hyperlink is the Android similar of Microsoft Circle of relatives Protection and is the most productive local software for the activity.
- Set up Circle of relatives Hyperlink: Obtain the “Google Circle of relatives Hyperlink for fogeys” app to your tool and the “Google Circle of relatives Hyperlink for kids & teenagers” app to your youngster’s tool.
- Hyperlink the Accounts: Apply the on-screen directions to hyperlink your youngster’s Google account for your guardian account.
- Organize Settings in Chrome:
- Open the Circle of relatives Hyperlink app to your (guardian’s) telephone and make a choice your youngster’s profile.
- Cross to “Controls” > “Content material restrictions” > “Google Chrome.”
- Make a selection “Simplest permit accepted websites.” That is the whitelist mode.
- Upload Authorized Web pages:
- Faucet on “Organize websites” > “Authorized.”
- Right here, you’ll manually upload the internet sites you need your youngster to get right of entry to. They are going to be blocked from all different websites.
iOS/iPadOS (The use of Display screen Time)
The method on an iPhone or iPad is just about just like the only on macOS.
- Open Settings: Cross to the “Settings” app.
- Make a selection Display screen Time: Faucet on “Display screen Time.”
- Content material & Privateness Restrictions: Cross to “Content material & Privateness Restrictions” and ensure the toggle is on.
- Content material Restrictions: Faucet on “Content material Restrictions,” then “Internet Content material.”
- Make a selection “Allowed Web pages Simplest”: That is probably the most direct approach to permit a whitelist. iOS supplies a default listing of child-friendly websites, however you’ll simply take away them and upload your personal.
- Upload Your Web pages: Faucet “Upload Web site” on the backside of the listing to construct your customized whitelist.
Means 4: Whitelisting on a Community Router
Whitelisting on the router point is among the maximum tough strategies as it applies to each and every tool attached for your community (Wi-Fi or stressed). This is a perfect resolution for a house or small place of business.
The precise steps range extensively between router producers and fashions, however the normal procedure is as follows:
- Get right of entry to Your Router’s Admin Panel:
- In finding your router’s IP cope with. It’s regularly imprinted on the router itself or will also be discovered on your pc’s community settings (it’s regularly 192.168.1.1 or 192.168.0.1).
- Open a internet browser and sort the IP cope with into the cope with bar.
- Log in with the router’s username and password (additionally regularly on a decal at the router).
- In finding the Content material Filtering or Parental Controls Segment: Search for settings classified “Parental Controls,” “Get right of entry to Regulate,” “Content material Filtering,” or “Web site Blocking off.”
- Allow Whitelist Mode:
- Many routers have a easy block/permit capability. It is very important search for a style that lets you “Block all web sites apart from…” or a an identical surroundings.
- Some routers require you to first set a rule to dam all site visitors after which create particular “permit” regulations for the internet sites to your whitelist. This may occasionally contain the use of wildcards (*) to dam the whole thing after which including your particular domain names.
- Input the Whitelisted Domain names: Upload the domains (e.g., elementor.com, google.com) to the listing of allowed websites.
- Practice the Laws: Save your settings and restart the router if induced. Now, any tool connecting for your community will likely be matter to those regulations.
Why Router-Degree Whitelisting is a Nice Possibility:
- Complete Protection: Protects all units, together with sensible TVs, gaming consoles, and visitor units.
- Tamper-Evidence: Customers at the community can not simply bypass the constraints with out get right of entry to to the router’s admin panel.
- Centralized Control: You solely have to regulate one listing for all your community.
For the ones enthusiastic about community regulate, making an investment in a router with powerful, user-friendly parental controls could be a profitable funding.
Means 5: The use of 3rd-Celebration Tool and Products and services
For max regulate, options, and straightforwardness of use, devoted third-party device is regularly your best option, particularly in enterprise environments.
- DNS Filtering Products and services (e.g., OpenDNS, CleanBrowsing): Those products and services paintings by way of redirecting your web site visitors thru their servers. You’ll be able to configure your router or particular person units to make use of their DNS servers after which arrange whitelists and blacklists thru a internet dashboard. This can be a very efficient and scalable resolution.
- Endpoint Safety Tool (e.g., Norton Circle of relatives, Kaspersky Secure Youngsters): Those are complete parental regulate suites that you simply set up on every tool. They provide whitelisting, closing dates, location monitoring, and detailed reporting. They’re most often very user-friendly however require a subscription and set up on each and every tool you need to give protection to.
- Unified Risk Control (UTM) Home equipment: In a company surroundings, a devoted {hardware} equipment (firewall) is the pro same old. Those units be offering granular regulate over all community site visitors, together with tough utility and internet filtering with complicated whitelisting features.
Construction and Managing Your Whitelist
Making a whitelist isn’t a one-time job. It calls for some preliminary effort and ongoing repairs to be efficient with out being overly restrictive.
Best possible Practices for Growing Your Preliminary Record
- Get started with the Necessities: Start by way of including absolutely the must-have web sites. For a piece pc, this would come with corporate web sites, cloud packages (Google Workspace, Administrative center 365), and very important equipment. For a kid, get started with their faculty portal, tutorial websites, and a couple of accepted leisure websites.
- Assume Extensively: Understand that web sites regularly depend on content material from different domain names. For instance, a web site would possibly pull fonts from fonts.googleapis.com or scripts from a Content material Supply Community (CDN) like cdn.jsdelivr.web. In case your whitelist is simply too strict, some websites won’t serve as as it should be. You might want to use your browser’s developer equipment (F12 key) to look what different domain names a web page is loading and upload them for your listing.
- Use a “Track First” Means: Some filtering equipment mean you can run in a non-blocking “track mode.” This allows you to see a log of all web sites visited over a couple of days. You’ll be able to use this log to construct a complete whitelist of vital websites earlier than you get started blocking off site visitors.
- Contain Your Customers: When you’re surroundings this up to your circle of relatives or workers, keep in touch the alternate. Ask them for a listing of web sites they want for his or her day by day actions. This fosters cooperation and decreases frustration.
Keeping up Your Whitelist
- Determine a Overview Procedure: Create a easy procedure for customers to request a brand new web site to be added to the whitelist. This can be a easy electronic mail request or a kind.
- Overview Requests Promptly: To steer clear of hindering productiveness or inflicting frustration, evaluate and act on requests in a well timed means.
- Steadily Audit the Record: Periodically evaluate your whitelist. Are there websites which can be now not wanted? Is a web site that used to be as soon as protected now doubtlessly problematic? A handy guide a rough audit each and every few months can assist stay the listing related and protected.
Demanding situations and Issues of Whitelisting
Whilst extremely efficient, whitelisting isn’t with out its demanding situations.
- Preliminary Setup Effort: Construction the preliminary whitelist will also be time-consuming, particularly for a big group.
- Over-Blocking off (False Positives): You’re going to inevitably block authentic and vital web sites. This is the reason having a transparent and fast procedure for including new websites is a very powerful.
- Capability Problems: As discussed, blocking off vital backend domain names (like CDNs) can destroy the capability of an allowed web site. This calls for some troubleshooting.
- Person Frustration: A restrictive surroundings will also be irritating for customers who’re aware of an open web. Transparent conversation in regards to the causes for the coverage is vital to managing this.
For lots of, making a web site with an excellent person revel in is a number one function. At Elementor, we offer equipment that provide you with entire design freedom. Simply as you sparsely craft the person revel in to your web site, whitelisting permits you to sparsely craft the surfing revel in to your customers or circle of relatives, prioritizing protection and focal point. Whether or not you’re construction a easy portfolio or a posh eCommerce web site with the WooCommerce Builder, controlling the virtual surroundings is a formidable idea.
Conclusion
Web site whitelisting is a proactive, tough safety technique that places you in entire regulate of your web revel in. Through adopting a “default deny” method, you create a essentially protected surroundings that protects in opposition to a limiteless array of on-line threats, from malware and phishing to undesirable distractions and irrelevant content material.
Whilst it calls for extra preliminary setup and ongoing control than conventional blacklisting, the advantages in safety, productiveness, and peace of thoughts are regularly smartly well worth the effort. Through selecting the proper way to your wishes—whether or not it’s a easy browser extension, your working components’s integrated equipment, or a network-wide router configuration—you’ll construct a more secure, extra targeted, and extra intentional virtual global for your self, your circle of relatives, or your company.
Often Requested Questions (FAQ)
1. What’s the major distinction between a whitelist and a blacklist? The primary distinction lies of their default rule. A whitelist follows a “default deny” coverage, which means it blocks each and every web site apart from the ones particularly indexed as accepted. A blacklist follows a “default permit” coverage, permitting get right of entry to to each and every web site apart from the ones particularly indexed as malicious or forbidden. Whitelisting is due to this fact a a lot more restrictive and protected method.
2. Is whitelisting 100% efficient in opposition to all on-line threats? No safety measure is 100% foolproof, however whitelisting is among the most efficient methods to be had. It protects in opposition to a person navigating to a recognized or unknown malicious web site. Alternatively, it wouldn’t give protection to in opposition to different danger vectors, akin to malicious electronic mail attachments, compromised device, or assaults that exploit a vulnerability in an allowed web site. It will have to be used as a part of a layered safety method that still comprises antivirus device, firewalls, and person schooling.
3. Will whitelisting decelerate my web connection? Most often, no. The method of checking a URL in opposition to a in the neighborhood saved or DNS-based whitelist is terribly rapid and should not have any noticeable have an effect on to your surfing pace. In some instances, by way of blocking off resource-heavy advertisements and scripts from unapproved websites, it might even fairly give a boost to web page load instances at the websites you do talk over with.
4. Can a tech-savvy youngster or worker bypass a whitelist? It is dependent upon the way it’s carried out.
- Browser Extensions: Simply bypassed by way of the use of a unique browser, disabling the extension in incognito mode, or uninstalling it if no longer password-protected.
- OS-Degree Controls (Circle of relatives Protection/Display screen Time): A lot tougher to avoid, as they require the guardian’s or administrator’s password to modify settings.
- Router-Degree Controls: Very tough to avoid for a regular person. They’d want to know the router’s admin password or attach to another community (like a cell hotspot) to get round it.
- VPNs: A Digital Non-public Community (VPN) can occasionally bypass whitelists, particularly the ones set on the router point. Extra complicated firewalls and safety device can establish and block VPN site visitors to stop this.
5. What will have to I do if a whitelisted web site isn’t operating as it should be? If an accepted web site is loading incorrectly (e.g., pictures are lacking, buttons don’t paintings), it’s most likely since the web site is determined by content material from different domain names that don’t seem to be to your whitelist. You’ll be able to use your browser’s Developer Equipment (normally by way of urgent F12), and have a look at the “Community” or “Console” tab to look which different URLs are being blocked. It is very important upload those vital backend domain names (like CDNs, API endpoints, or font libraries) for your whitelist to revive complete capability.
6. Is there a approach to whitelist a whole class of web sites as a substitute of one after the other? Sure, however this capability is generally discovered in additional complicated third-party device and DNS filtering products and services (like OpenDNS or CleanBrowsing). Those products and services categorize thousands and thousands of web sites (e.g., “Training,” “Social Media,” “Information”) and mean you can block or permit whole classes directly, which will also be a lot more environment friendly than managing a handbook listing.
7. How does whitelisting paintings for packages and methods? The idea that is similar. Utility whitelisting, regularly utilized in high-security company environments, prevents any device from operating until its executable document is on a pre-approved listing. That is extraordinarily efficient at combating customers from putting in unauthorized device or operating malware that has been downloaded to the gadget. Home windows Defender Utility Regulate is an instance of this.
8. Can I whitelist particular YouTube channels or movies? This can be a commonplace and difficult request for fogeys. Usual URL whitelisting can solely permit or block youtube.com as an entire. To regulate content material inside of YouTube, you want to make use of YouTube’s personal options. The most efficient way is to make use of YouTube Youngsters, which gives a curated, more secure surroundings. For older kids, you’ll use “Limited Mode” at the major YouTube web site, despite the fact that it isn’t a great filter out. Some third-party parental regulate device additionally provides extra granular controls for platforms like YouTube.
9. What’s the very best whitelisting resolution for a small enterprise? For a small enterprise, a multi-layered method is very best.
- Router/Firewall: Put in force a business-grade router or firewall that helps content material filtering and whitelisting. This units the baseline for all the community.
- DNS Filtering: A carrier like OpenDNS Umbrella provides a easy, cloud-based approach to put in force internet insurance policies throughout your community or even on roaming laptops.
- Endpoint Coverage: Use equipment like Microsoft Team Coverage or an endpoint control option to put in force browser settings and save you customers from putting in unauthorized device that would bypass community filters.
10. How can I am getting began with a easy whitelist for my private pc? The best way to begin is with a browser extension. Set up a credible extension like “BlockSite” for Chrome or Firefox. Start by way of making a whitelist of the 10-15 web sites you utilize maximum continuously for paintings or private duties. Then, permit the “block all different websites” function. Use this for an afternoon. You’re going to temporarily uncover different very important websites you forgot so as to add. This trial-and-error method is a low-stakes approach to know how whitelisting feels and construct a sensible listing with out committing to a system-wide alternate in an instant.